NSA: Inside the FIVE-EYED VAMPIRE SQUID of the INTERNET
First published by The Register -
http://www.theregister.co.uk/2014/06/05/how_the_interenet_was_broken/
One year after The Guardian opened up the trove of top secret American and British documents leaked by former National Security Agency (NSA) sysadmin Edward J Snowden, the world of data security and personal information safety has been turned on its head.
Everything about the safety of the internet as a common communication medium has been shown to be broken. As with the banking disasters of 2008, the crisis and damage created - not by Snowden and his helpers, but by the unregulated and unrestrained conduct the leaked documents have exposed - will last for years if not decades.
Compounding the problem is the covert network of subornment and control that agencies and collaborators working with the NSA are now revealed to have created in communications and computer security organisations and companies around the globe.
The NSA's explicit objective is to weaken the security of the entire physical fabric of the net. One of its declared goals is to "shape the worldwide commercial cryptography market to make it more tractable to advanced cryptanalytic capabilities being developed by the NSA", according to top secret documents provided by Snowden.
Profiling the global machinations of merchant bank Goldman Sachs in Rolling Stone in 2009, journalist Matt Taibbi famously characterized them as operating "everywhere ... a great vampire squid wrapped around the face of humanity, relentlessly jamming its blood funnel into anything that smells like money”.
The NSA, with its English-speaking "Five Eyes" partners (the relevant agencies of the UK, USA, Australia, New Zealand and Canada) and a hitherto unknown secret network of corporate and government partners, has been revealed to be a similar creature. The Snowden documents chart communications funnels, taps, probes, "collection systems" and malware "implants" everywhere, jammed into data networks and tapped into cables or onto satellites.
The evidence Snowden has provided, by the bucketload, has shown that no country, no network, no communications system, no type of communication has been too small or trivial or irrelevant to attract attention and the ingestion of data into huge and enduring archives - under construction at NSA headquarters and already in operation at its new Utah Data Center.
Operations have ranged from the systematic recording of every mobile telephone call in the tiny 380,000 population Bahamas, through Angry Birds, World of Warcraft, Second Life, intimate Yahoo webcam images and direct cyber attacks on the data centre networks of Google (carried out by British allies at GCHQ from bases in the UK). Under the covernames of WINDSTOP and MUSCULAR, GCHQ data from UK cable taps, including direct intercepts of US email providers and ISPs, is provided wholesale to NSA. NSA has also deployed two overseas Remote Operations centres for malware management at Menwith Hill Station in Yorkshire and at Misawa, Japan.
There are parallels to the banking world, too, in the pervasive and longstanding networks of influence that have been created with the aim of influencing and controlling policymakers, and which have assured minimal political change when damage is done. Merchant banks like Goldmans have long worked hard to have their alumni in positions of political power and influence, in control at vital times.

Oman spy base revealed in The Register as part of GCHQ's £1bn project TEMPORA
Last month, accompanying his new book Nowhere to Hide, journalist Glenn Greenwald has published 180 new Snowden documents that lay out the NSA's global reach - 33 "Third Party" countries, 20 major access "choke points" accessing optical fibre communications, 80 "strategic partner" commercial manufacturers, 52 US, UK and overseas satellite interception sites, more than 80 US Embassies and diplomatic sites hosting floors packed with surveillance and monitoring equipment, and over 50,000 "implants" - malware and tampered hardware that has rendered most commercial VPN systems and software transparent to the NSA and its partners.
In GCHQ and NSA Sigint (signals-intelligence) jargon, common or garden "hacking" is never talked about: the insider term for such activity is "CNE" - Computer Network Exploitation.
NSA's access to optical fibre cables worldwide can be "covert, clandestine or co-operative," according to one of the leaked slides. The covert operations described in the Snowden documents include secret taps on other companies' cables installed by employees of such firms as AT&T and BT.
The published Snowden documents have not yet described NSA's special activities to get into cables even their overseas and corporate partners cannot access. For more than ten years, an adapted nuclear submarine - the USS Jimmy Carter - has installed underwater taps on marine cables, "lifting them up", installing taps and then laying out "backhaul" fibres to interception sites, according to a former Sigint employee. Cable companies have speculated that the submarine tapping activity may be connected to a rash of unexplained cable cuts in recent times affecting fibre cables in the Middle East and South Asia; the cable breaks could serve to prevent operators noticing as taps were installed elsewhere on the same cable.
One previously unrevealed outstation of Britain's secret internet tapping programme has been operating for almost five years in the autocratic Persian gulf state of Oman, according to documents obtained by Snowden in Hawaii. The station, known as Overseas Processing Centre 1 (OPC-1) is part of GCHQ’s massive £1bn project TEMPORA, which GCHQ wants to use to harvest all internet communications it can access and hold that data for up to 30 days.
The damage created to IT security is deliberate, sustained and protected even inside the agencies' compartmented planning cells by arcane contrivances of language. Breaking the safety and value of crypto systems, in sigint speak, is "enabling". Deliberately sabotaging security, in the inverted Orwellian world of the sigint agencies is said to be "improving security".
According to the leaked, detailed current US intelligence budget provided by Snowden, NSA's "Sigint Enabling Project ... actively engages the US and Foreign IT industries to covertly influence and/or overtly leverage their commercial products' designs. These design changes make the systems in question exploitable through SIGINT collection ... with foreknowledge of the modification. To the consumer and other adversaries, however, the systems' security remains intact."
Despite apologists' denials, the language of this major US government document is unambiguous in describing broken crypto and hardware and software "backdoors" as a much-desired NSA goal.

Top US companies are among more than 80 helping NSA "enable" backdoors and breaks in security protection, according to a top secret slide revealed by Edward Snowden
Tricking a company like RSA Security into promoting backdoored and sabotaged algorithms for default use in security products is "enabling". Physically sabotaging Cisco routers while they are being shipped out of the US to commercial customers - a serious crime when committed by anyone but the Federal Bureau of Investigation and the NSA - is "enabling".
Ensuring that communications security encryption chips "used in Virtual Private Networks and Web encryption devices" secretly ship with their security broken open, as specified in the current US "cryptologic capabilities plan", is "enabling". In the coming year, NSA's budget for such Sigint "enabling" is $255m.
Who plays in this corporate "enabling" game?
Since the days of Watergate in the 1970s, and the subsequent US Congressional investigations, AT&T - the world's 23rd largest company - has been identified as providing US government access to all its customers' communications passing in and out of the US. The intercepted communications passed on long ago included communications of 1960s US antiwar dissidents.
AT&T's secret role intercepting Americans' communications in a programme dubbed SHAMROCK was flushed out by Congressional enquiries in 1975, and largely stopped as illegal - for a few years. But it all began again in 1978 when a new US Foreign Intelligence Surveillance Act was passed. SHAMROCK was reborn, the Snowden archive reveals, as BLARNEY. In the bizarre and boastful world of show-off Powerpoints that NSA geeks prepare for their colleagues, BLARNEY even has its own logo.
The identity of NSA's and GCHQ's corporate industrial and international partners are amongst the Sigint agencies' most closely guarded secrets. There are strict internal prohibitions in the US and the UK against revealing the true corporate identities behind covernames like FAIRVIEW or STORMBREW, both identified as providing "upstream" (meaning fibre cable tap) access to Microsoft, Yahoo, Google, and many other companies' internet communications.
More than once, the Snowden documents have revealed that siginters' NSA braggadocio can let cover slip. Among the new Snowden documents published last month by Greenwald is a potentially devastating slide listing NSA commercial "Strategic Partnerships".
The slide displays, with corporate logos, the names of major US IT companies who are listed under NSA's vaunted "alliances with over 80 Major Global Corporations". The companies identified are said to be "supporting both missions": that is, both Sigint attacks on global communications networks, and the more acceptable public face of collaboration - cyber defence activity.
The roll call of names and logos on the slide include most of the US's IT industry giants: Microsoft, HP, Cisco, IBM, Qualcomm, Intel, Motorola, Qwest, AT&T, Verizon, Oracle and EDS.
This document and many more like it shine a spotlight on the invidious position in which major US corporations have found themselves. Their trust has been compromised, with share valuations now tumbling to follow. Cisco, despite being reported as "supporting missions" in the classified slides, was reportedly devastated when last month Greenwald published photographs taken by NSA's hacking department of "interdicted" Cisco equipment, stolen in transit and then put back in the delivery system after being tampered with to open the kit up for NSA remote control.

NSA staff pictured breaking into to secretly divert Cisco shipments of equipment, so as to insert covert "beacons" to compromise the networks they support
The US corporations have also helped spy on their communications partners, both overtly and covertly, according to the documents. FAIRVIEW, a corporate partner "with access to int. cables, routers, switches", according to one recently published note "operates in the US, but has access to information that transits the nation and through its corporate relationships provides unique accesses to other telecoms and ISPs".
It is also "aggressively involved in shaping traffic to run signals of interest past our monitors". For these and other services, according to the classified US Intelligence budget leaked by Snowden to the Washington Post, FAIRVIEW will receive $95m from NSA in the current year.
According to another slide Greenwald has published this month, STORMBREW operates seven "choke points" on international communications on the US eastern and western seaboards, each covernamed for leading US ski resorts.
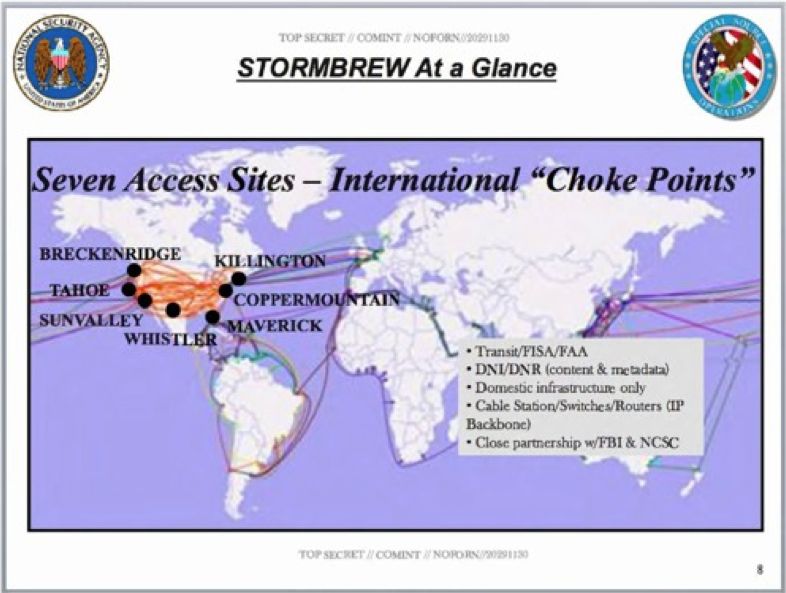
Verizon, codenamed STORMBREW by NSA has "choke points" on US communications
FAIRVIEW and STORMBREW are the covernames for the US's communications giants, AT&T and Verizon. In the UK, BT (GCHQ covername "REMEDY") and Verizon/Vodafone (GCHQ covername "GERONTIC") are described as actively intercepting their own and other companies' fibre networks, and linking them to GCHQ's processing sites at Cheltenham and Bude, Cornwall. BT and Verizon are also lavishly remunerated by GCHQ for their work in providing access to communications links in the UK, receiving payments of tens of millions of pounds annually, according to documents copied by Snowden.
In one of the most alarming slideshows, NSA's successes in smashing basic general internet cryptography security is described in classic style as "improving security". NSA's project BULLRUN was described thus:
For the past decade, NSA has led an aggressive, multipronged effort to break widely used Internet encryption technologies ... Cryptanalytic capabilities are now coming online. Vast amounts of encrypted Internet data which have up till now been discarded are now exploitable. Major new processing systems ... must be put in place to capitalise on this opportunity.
Listeners at this talk were also warned that the "groundbreaking capabilities" were "extremely fragile ... do not ask about or speculate on sources or methods". "Indoctrination" - special security briefings and signing new warnings - was required for access to information about how BULLRUN techniques work.
In the creation of such arcane rituals of access to sacred secrets that no-one may know and to the power they are believed to bestow, working life inside Sigint communities can seem to resemble nothing so much as the medieval churches. Like Latin chanted by medieval priests, NSA and GCHQ's extraordinary lexicons of "covernames" revealed by Snowden are all in fact unclassified - even BULLRUN. The ordinary mortal may hear them, but must never know their meanings, which are protected behind layers of secrecy beyond Top Secret: in the US, ECI for Extremely Compartmented Information, in the UK, STRAP 1, STRAP 2 or STRAP 3.
In another Snowden document prepared by NSA's Cryptanalysis and Exploitation Services unit in 2010, Project BULLRUN is described as involving "multiple sources, all of which are extremely sensitive. They include CNE [Computer Network Exploitation], interdiction, industry relationships, collaboration with other IC [Intelligence Community] entities, and advanced mathematical techniques".
The covert nature of NSA's relationships and their power to influence policy and compromise internet security technologies was unguardedly summarised in a chatty top secret blog provided by NSA's Foreign Affairs Directorate in 2009 and leaked by Snowden.
"What are we after with our third party relationships?" asked the spies.
In summary, the answer is that they get to wiretap their own countries and their neighbours, places to which NSA and GCHQ otherwise could not legally reach.
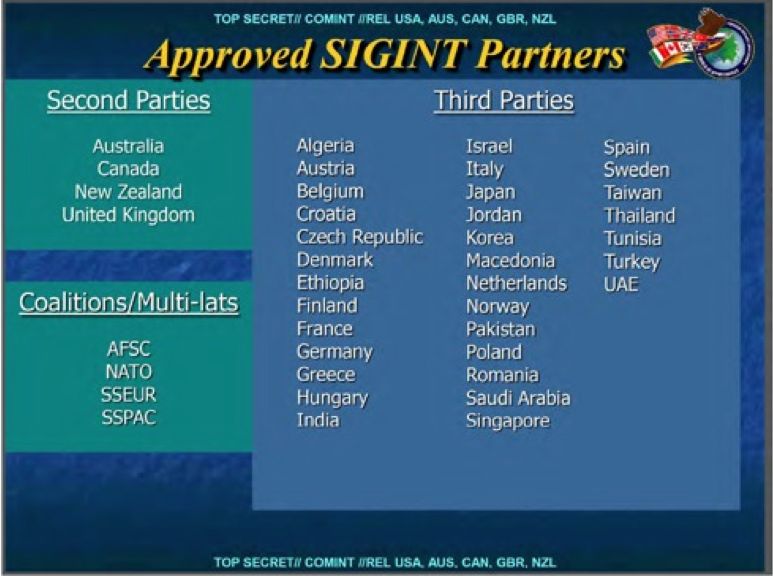
NSA's approved list of Second and Third Party partners
In return, collaborating allies may get high tech toys to impress their own masters - and better ones if they are willing to break rules or laws. According to the Foreign Affairs Directorate blog:
"NSA might be willing to share advanced technologies in return for that partner's willingness to do something politically risky."
The Third Party relationships with other nations' spooks and/or secret police are often kept secret even from the foreign governments in question, according to the blog:
"In many of our foreign partners' capitals, few senior officials outside of the defence-intelligence apparatuses are witting to any SIGINT connection to the USA/NSA."
Documents provided by Snowden show that GCHQ particularly prizes the data they get from Sweden, Israel and India.
A year past the first revelations, the US has begun a debate, as Snowden hoped, and changes and restrictions affecting American citizens' communications have started. But for foreigners, there is nothing. In the UK and across Europe, there has been much anger but little change. The new Snowden documents provide some of the answer, showing that virtually every EU member state has a covert surveillance "Sigint Exchange Agreement" with NSA. None of these agreements have been reported to or agreed by national parliaments.
The only European countries apparently not signed up to help break the internet are Luxembourg, Switzerland, Monaco, and Ireland. And Iceland.
That is the reach of the embrace of the internet's vampire squid. ®